Cybersecurity researchers shed light on sophisticated mobile phishing (aka mishing) company that is intended to distribute the updated version Antidote banking trojan.
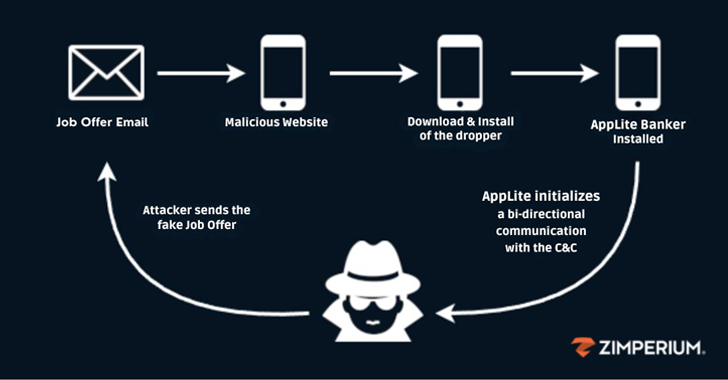
“Attackers posed as recruiters, luring unsuspecting victims with job offers,” Zimperium zLabs researcher Vishnu Pratapagiri said in a new report.
“As part of the fraudulent recruitment process, the phishing company forces victims to download a malicious application that acts as a dropper, ultimately installing an updated variant of Antidot Banker on the victim’s device.”
New version Malicious programs for Android has been codenamed AppLite Banker by a mobile security company, highlighting its ability to scramble a PIN (or pattern or password) and remotely take control of infected devices, a feature that was also recently seen in TrickMo.
The attacks use a variety of social engineering strategies, often luring targets with the prospect of an employment opportunity that claims to offer “competitive wages of $25 an hour” and excellent career opportunities.
In a Message for September 2024 identified by The Hacker News on Reddit, several users said they received emails from a Canadian company called Teximus Technologies about a job opening for a remote customer service agent.
When a victim interacts with the alleged recruiter, they are prompted to download a malicious Android app from a phishing page as part of the recruitment process, which then acts as the first stage responsible for facilitating the deployment of the underlying malware on the device.
Zimperium says it has discovered a network of fake domains being used to distribute malware APKs masquerading as customer relationship management (CRM) software.
Dropper applications other than use Manipulation with ZIP files to evade analysis and bypass security protections, tell victims to sign up for an account, then a message will be displayed asking them to install an app update to “keep your phone secure.” It also recommends that they allow the installation of Android apps from external sources.
“When the user clicks the ‘Update’ button, a fake Google Play Store icon appears, which leads to the installation of malware,” Pratapagiri said.
“Like its predecessor, this malicious app requests and abuses Accessibility Services permissions to overlay the device’s screen and perform malicious actions. These actions include self-granting permissions to facilitate further malicious operations.”
The latest version of Antidot supports new commands that allow operators to trigger Keyboard and Input settings, interact with the lock screen based on a given value (such as a PIN, pattern or password), wake the device from sleep mode. , reduce screen brightness to the lowest level, launch overlays to steal Google account credentials, and even prevent it from being deleted.
It also includes the ability to hide certain SMS messages, block calls from a pre-set set of mobile numbers obtained from a remote server, run “Default Application Management” settings, and serve fake login pages to 172 banks, cryptocurrency wallets, and social networks. services such as Facebook and Telegram.
Some of the other known features of the malware include keylogging, call forwarding, SMS theft, and Virtual Networking (VNC) functionality for remote interaction with compromised devices.
Users who speak languages such as English, Spanish, French, German, Italian, Portuguese and Russian are said to be targeted by the campaign.
“Given the advanced capabilities of malware and the extensive control over compromised devices, it is critical to implement proactive and robust defenses to protect users and devices from this and similar threats, preventing data loss or financial loss.”
The findings come after Cyfirma revealed that high-value assets in South Asia were targeted by an Android malware campaign that provides SpyNote Trojan. The attacks have not been attributed to any known threat actors or groups.
“The continued use of SpyNote is notable as it highlights the preference of threat actors to use this tool to target prominent individuals, despite its public availability on various underground forums and Telegram channels,” the company said in a statement. said.