Ukraine’s Computer Emergency Response Team (CERT-UA) has warned of a new series of cyber attacks that it says have targeted the country’s defense companies, as well as its security and defense forces.
Phishing attacks have been attributed to a Russian-linked threat called UAC-0185 (aka UNC4221), which has been in effect since at least 2022.
“Phishing letters imitated the official messages of the Ukrainian Union of Industrialists and Entrepreneurs”, — CERT-UA said. “The e-mails advertised a conference held on December 5 in Kyiv aimed at bringing the products of domestic defense industry enterprises into compliance with NATO standards.”
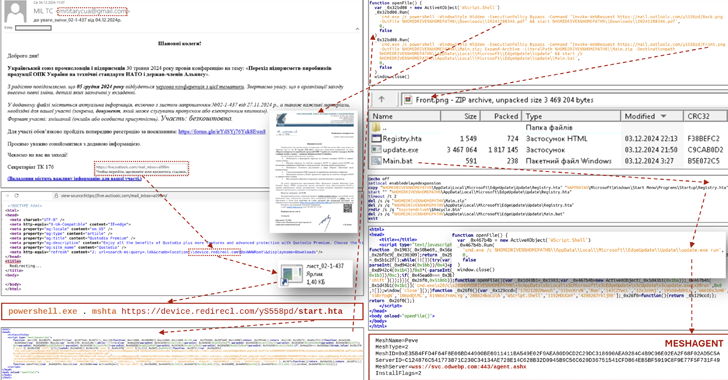
Embedded in the email message is a malicious URL that encourages recipients to click on it to view “important information” related to their participation in the conference.
But what it actually does is download a Windows shortcut file that, when opened, is designed to run an HTML application, which in turn contains JavaScript code responsible for executing PowerShell commands capable of loading the next stage’s payloads.
This includes a decoy file and a ZIP archive containing a batch script, another HTML application, and an executable file. The final step runs a batch script to run the HTML application file, which then runs MeshAgent binary file on the host, giving attackers remote control over the compromised system.
CERT-UA said the threat is primarily focused on stealing credentials associated with messaging apps like Signal, Telegram, and WhatsApp, and Ukrainian military systems like DELTA, Teneta, and Kropyva.
“Hackers also carried out a number of cyberattacks with the aim of obtaining unauthorized access to the computers of employees of defense enterprises and representatives of law enforcement agencies,” the agency noted.
According to Google-owned Mandiant, which disclosed UNC4221 on SentinelLabs LABScon security conference in early September this year, the threat actor of course for collecting “data related to the battlefield through the use of Android malware, phishing operations masquerading as Ukrainian military programs, and operations targeting popular messaging platforms such as Telegram and WhatsApp.”