A newly discovered malware campaign was found to be targeting private users, retailers and businesses serving primarily in Russia to deliver NetSupport RAT and BurnsRAT.
Company, dubbing Horns and hooves from Kaspersky, from the beginning of March 2023. more than 1,000 people were injured. The ultimate goal of these attacks is to use the access provided by these Trojans to install malicious hijackers such as Rhadomantis and Medusa.
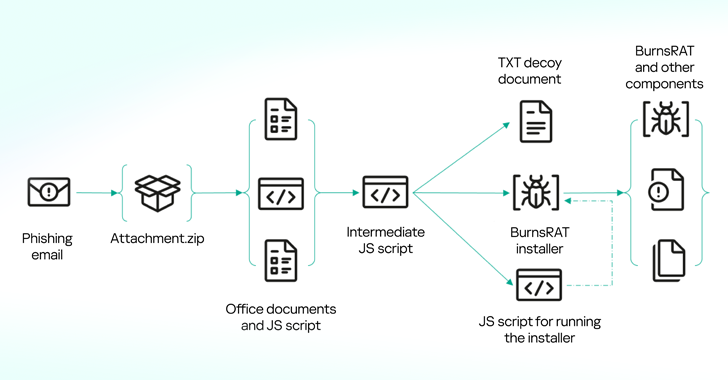
“In recent months, there has been a surge in mailings with similar email attachments in the form of a ZIP archive containing JScript scripts,” security researcher Artyom Ushkov said in Monday’s analysis. “Script files (disguised) as requests and bids from potential customers or partners.”
The threat actors behind the operations demonstrated their active development of the JavaScript payload, making significant changes throughout the campaign.
In some cases, the ZIP archive has been found to contain other documents associated with an impersonated organization or person in order to make a phishing attack more likely to succeed and trick recipients into opening the malicious software file.
One of the earliest samples identified by the campaign is an HTML application (HTA) file that, when run, downloads a dummy PNG image from a remote server using the curl utility for Windows, and stealthily retrieves and executes another script (” bat_install.bat”) from another server using BITSAdmin command line tool.
The newly downloaded script then proceeds to retrieve several other files with BITSAdmin, including the NetSupport RAT malware, which establishes contact with the command and control (C2) server created by the attackers.
The next iteration of the campaign, observed in mid-May 2023, included a JavaScript intermediate that mimics legitimate JavaScript libraries such as Next.js to activate the NetSupport RAT infection chain.
Kaspersky said it also found another variant of the JavaScript file that removed the NSIS installer, which is then responsible for deploying the BurnsRAT on the compromised host.
“Although the backdoor supports commands for downloading and running files remotely, as well as various methods of executing commands through the Windows command line, the main task of this component is to run the Remote Manipulator System (RMS) as a service and send the RMS session ID to the attackers’ server,” explained Ushkov.
“RMS is an application that allows users to interact with remote systems over a network. It enables desktop management, command execution, file transfer, and data sharing between devices located in different geographic locations.”
In a sign that threat actors are continuing to fine-tune their modus operandi, two other attack sequences seen in late May and June 2023 came with a completely reworked NetSupport RAT installation BAT file and embedded the malware directly into JavaScript code, respectively .
There are indications that the campaign is the work of a threat known as TA569 (aka Gold Prelude, Mustard Tempest and Purple Vallhund) who is known for working with SocGholish (aka FakeUpdates) malware. This connection results from an overlap in the NetSupport RAT license and configuration files used in the associated actions.
It should be noted that TA569 was also known act as the initial access broker for subsequent ransomware attacks such as WastedLocker.
“Depending on whose hands this access falls into, the consequences for victim companies can range from data theft to encryption and damage to systems,” Ushkov said. “We have also observed attempts to install theft on some infected machines.”