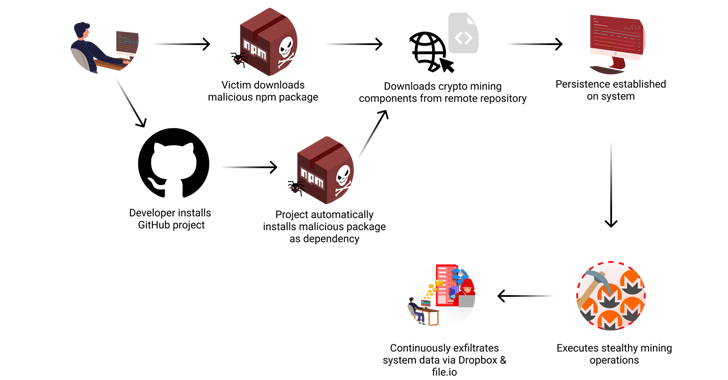
Cybersecurity researchers discovered a software supply chain attack that remained active for more than a year in the npm package registry, starting with an innocuous library and later adding malicious code to steal sensitive data and mine cryptocurrency from infected systems.
Package, no @0xengine/xmlrpcwas originally published on October 2, 2023. as a JavaScript-based XML-RPC server and client for Node.js. To date, it has been downloaded 1790 times and remains available for download from the repository.
Checkmarxwho discovered the package said that the malicious code was strategically injected into version 1.3.4 every other day, containing functionality to collect valuable information such as SSH keys, bash history, system metadata and environment variables every 12 hours and filter it through such services like Dropbox and file.io.
“The attack achieved propagation through several vectors: a direct npm installation and as a hidden dependency in a repository that looks legitimate,” security researcher Yehuda Gelb. said in a technical report published this week.
The second approach involves a GitHub project repository called yawpp (short for “Yet Another WordPress Poster”), which purports to be a tool designed to programmatically create posts on the WordPress platform.
Its “package.json” file. lists the latest version of @0xengine/xmlrpc as a dependency, causing a malicious npm package to be automatically downloaded and installed when users try to configure the yawpp tool on their systems.
It is currently unclear whether the tool’s developer intentionally added this package as a dependency. The repository has been forked once at the time of writing. Needless to say, this approach is another effective method of spreading malware, as it exploits users’ trust in package dependencies.
Once installed, the malware is designed to collect system information, install security on the host via systemd, and deploy the XMRig cryptocurrency miner. 68 compromised systems were found to be actively mining cryptocurrency through the attacker’s Monero wallet.
In addition, it is equipped to constantly monitor the list of running processes to check for commands such as top, iostat, sar, glances, dstat, nmon, vmstat and ps, and stop all mining-related processes if found. It is also capable of suspending mining operations when user activity is detected.
“This discovery serves as a stark reminder that a package’s longevity and consistent maintenance history do not guarantee its safety,” Gelb said. “The software supply chain requires constant vigilance both during initial inspection and throughout the package’s lifecycle, whether they are initially malicious packages or legitimate packages compromised through updates.”
Disclosure occurs as Datadog Security Labs have discovered an ongoing malware campaign targeting Windows users that uses fake packages uploaded to both npm repositories and the Python Package Index (PyPI) with the ultimate goal of deploying open-source malware known as Blank-Grabber and Skuld Stealer .
The company that discovered the supply chain attack last month is tracking a threat cluster called MUT-8694 (where MUT stands for “Mysterious Unattributed Threat”), saying it matches the company that was documented Socket earlier this month in an attempt to infect Roblox users with the same malware.
As many as 18 and 39 fake unique packages have been uploaded to npm and PyPI, with the libraries attempting to pass off as legitimate packages using typosquatting techniques.
“The use of multiple packages and the involvement of multiple malicious users suggests that MUT-8694 is persistently trying to compromise developers,” Datadog researchers said. “Unlike the PyPI ecosystem, most npm packages had references to Roblox, an online game creation platform, suggesting that the threat actor is targeting Roblox developers specifically.”