A threat actor known as APT-C-60 was linked to a cyberattack targeting an unnamed organization in Japan that used a job application-themed lure to deliver the SpyGlace backdoor.
This follows JPCERT/CC findings, which say the intrusion used legitimate services such as Google Drive, Bitbucket and StatCounter. The attack was carried out around August 2024.
“In this attack, an email purporting to be from a potential employee was sent to a recruiting contact, infecting the contact with malware,” the agency reported. said.
APT-C-60 is an alias appointed a cyberespionage group known to target East Asian countries. In August 2024 A remote code execution vulnerability in WPS Office for Windows (CVE-2024-7262) was observed to exploit a custom backdoor named SpyGlace.
The attack chain identified by JPCERT/CC involves the use of a phishing email containing a link to a file located on Google Drive, a virtual hard disk (VHDX) file that, when downloaded and mounted, contains a decoy document and a Windows Shortcut (“Self-Introduction .lnk”).
The LNK file is responsible for triggering the next steps in the infection chain while displaying a decoy document to distract attention.
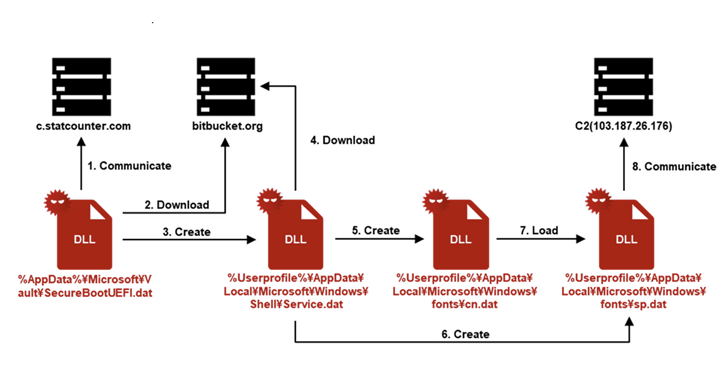
This entails launching a bootloader/dropper payload called “SecureBootUEFI.dat”, which in turn uses StatCounter, a legitimate web analytics tool, to pass a string that can uniquely identify the victim device using HTTP link field. The string value is derived from the computer name, home directory, and username and encoded.
The downloader then accesses Bitbucket using the encoded unique string to get the next stage, a file known as “Service.dat”, which downloads two more artifacts from another Bitbucket repository – “cbmp.txt” and “icon.txt”. – which are saved as “cn.dat” and “sp.dat” respectively.
“Service.dat” also stores “cn.dat” on the compromised host using the named method Hijacking COMafter which the latter runs the SpyGlace backdoor (“sp.dat”).
The backdoor, for its part, makes contact with the command and control server (“103.187.26(.)176”) and waits for further instructions that allow it to steal files, download additional plugins, and execute commands.
It should be noted that cyber security firms Chuangyu 404 Laboratory and Positive technologies independently reported identical SpyGlace malware distribution campaigns, highlighting evidence pointing to APT-C-60 and APT-Q-12 (aka pseudo-hunter), being subgroups of DarkHotel cluster.
“Groups from the Asian region continue to use unconventional methods to deliver their malware to victim devices,” Positive Technologies said. “One of these techniques is the use of virtual disks in VHD/VHDX format to bypass the security mechanisms of the operating system.”