Cybersecurity researchers have uncovered a new phishing kit that has been used in campaigns targeting Australia, Japan, Spain, the UK and the US since at least September 2024.
Netcraft reported that more than 2,000 phishing websites have identified a set known as Xiū gǒu, with a proposal used in attacks targeting various verticals such as the public sector, postal services, digital services and banking services.
“Threat objects using the kit to deploy phishing websites often rely on Cloudflare’s anti-bot and hosting obfuscation capabilities to prevent detection,” Netcraft said in a report released Thursday.
Some aspects of the phishing kit have been documented by security researchers Will Thomas (@ BushidoToken) and Fox_threatintel (@banthisguy9349) last month.
Phishing kits like Xiū gǒu are dangerous because they can lower the barrier to entry for less skilled hackers, potentially leading to an increase in malicious campaigns that can lead to the theft of sensitive information.
Xiū gǒu, which is developed by a Chinese-speaking threat actor, provides users with an admin panel and is developed using technologies such as Golang and Vue.js. The kit is also designed to steal credentials and other information from fake phishing pages hosted on the “.top” top-level domain via Telegram.
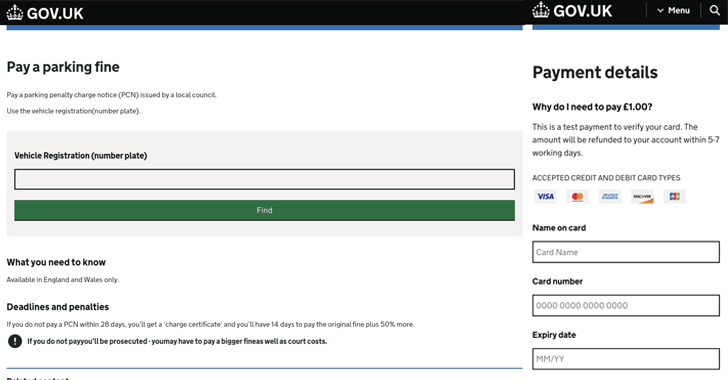
Phishing attacks are distributed using Rich Communications Services (RCS) messages, rather than SMS, which warn recipients of alleged parking fines and failed package deliveries. The messages also instruct you to click on a link shortened by a URL shortening service to pay a fine or update your shipping address.
“Fraudsters usually manipulate victims into providing their personal details and making payments, such as to return a parcel or pay a fine,” Netcraft said.
RCS, which is primarily available through Apple Messages (starting with iOS 18) and Google Messages for Android offers users an upgraded messaging experience with support for file sharing, input indicators and additional support for end-to-end encryption (E2EE).
In a blog post late last month, the tech giant in detail new protections needed to combat phishing, including the deployment of improved fraud detection using on-device machine learning models to specifically filter fraudulent messages related to package delivery and employment opportunities.
Google also said it was piloting security alerts when users in India, Thailand, Malaysia and Singapore received text messages from unknown senders with potentially dangerous links. The new protections, which are expected to be rolled out globally later this year, also block messages containing links from suspicious senders.
Finally, Search Specialist adds the ability to “automatically hide messages from international senders who are not contacts” by moving them to the Spam and Blocked folder. The feature was first enabled on a pilot basis in Singapore.
The disclosure comes after Cisco Talos revealed that users of Facebook business and advertising accounts in Taiwan were targeted by an unknown threat actor in a phishing campaign designed to deliver malware such as Lumma or Rhadamanthys.
The decoy messages come with a link that, when clicked, takes the victim to a Dropbox or Google Appspot domain, triggering the download of a RAR archive containing a fake executable PDF file that serves as a conduit for downloading the hijacker malware.
“Phishing email and fake PDF file names are designed to impersonate a company’s legal department in an attempt to lure the victim into downloading and running the malware,” Joey Chen, Talos researcher. saidadding that operations continue from July 2024.
“The emails demand that the infringing content be removed within 24 hours, cease further use without written permission, and warn of possible legal action and claims for compensation for failure to comply.”
Phishing campaigns mimicking OpenAI have also been observed targeting businesses around the world, telling them to immediately update their payment information by clicking on a confusing hyperlink.
“This attack was sent from a single domain to more than 1,000 recipients,” Barracuda says said in the report. “However, the email used various hyperlinks in the body of the email, possibly to avoid detection. The email passed DKIM and SPF checks, which means the email was sent from a server that is authorized to send emails on behalf of the domain. However, the domain itself is suspicious.”