A now-fixed security flaw in the Opera web browser could have allowed a malicious extension to gain unauthorized full access to private APIs.
A code-named attack CrossBarkingcould enable actions such as capturing screenshots, changing browser settings and account theft, Guardio Labs said.
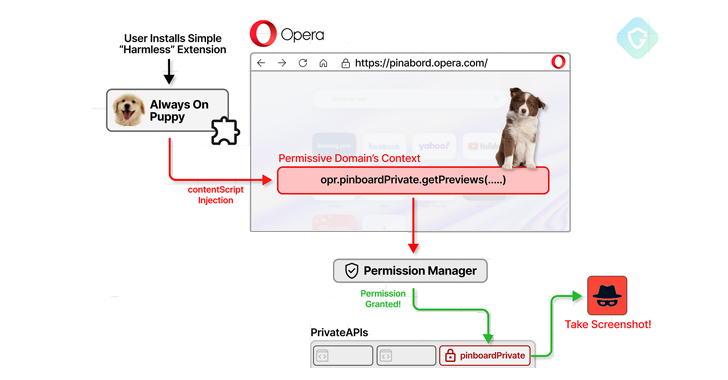
To demonstrate the problem, the company said it managed to publish a seemingly harmless browser extension to the Chrome Web Store, which could then exploit the flaw when installed in Opera, making it an example of a cross-browser attack on the store.
“This case study not only highlights the perennial clash between performance and security, but also provides a fascinating look at the tactics used by today’s threat actors that operate just below the radar,” Nati Tal, Head of Guardio Labs, said in a report shared with The Hacker News.
There was a problem addressed Opera as of September 24, 2024 after responsible disclosure. However, this is not the first time the browser has been exposed to security flaws.
Earlier in January of this year, details of the vulnerability, which is tracked as MyFlaw which uses a legitimate feature called My Flow to execute any file on the underlying operating system.
The latest attack technique is based on the fact that several public subdomains owned by Opera have privileged access to private APIs built into the browser. These domains are used to support specific Opera features such as Opera Wallet, Pinboard and others, as well as those used in internal development.
Some domain names which also include certain third party domains are listed below –
- crypto-corner.op-test.net
- op-test.net
- gxc.gg
- opera.atlassian.net
- pinboard.opera.com
- instagram.com
- yandex.com
While sandboxing ensures that the browser context remains isolated from the rest of the operating system, Guardio’s research found that content scripts present in a browser extension can be used to inject malicious JavaScript into over-permitted domains and gain access to private APIs.
“The content script does have access to the DOM (Document Object Model),” Tal explained. “This includes being able to change it dynamically, in particular by adding new elements.”
Armed with this access, an attacker can take screenshots of all open tabs, extract session cookies to hijack accounts, and even change a browser’s DNS-over-HTTPS (DoH) settings to resolve domains through a DNS server controlled by the attacker.
This can then set the stage for powerful adversary-in-the-middle (AitM) attacks, where victims attempt to visit bank or social networking sites by redirecting them to their malicious counterparts.
For its part, the malicious extension could have been published as something harmless in any of the add-on catalogs, including the Google Chrome Web Store, where users could download and add it to their browsers, effectively triggering the attack. However, permission is required to run JavaScript on any web page, especially on domains that access private APIs.
with fake browser extensions repeatedly infiltrating official stores, not to mention some legitimate ones lacks transparency in their data collection practices, the findings highlight the need for caution before establishing them.
“Browser extensions have a lot of power—for better or for worse,” Tal said. “Therefore, the policy enforcement agencies must strictly monitor them.”
“The current verification model is inadequate; we recommend backing it up with additional manpower and continuous analysis methods that monitor extension activity even after approval. Also, performing valid identity verification for developer accounts is critical, so simply using a free email and prepaid credit card is not enough to sign up.”