Russian-speaking users have been targeted by a new phishing campaign that uses an open-source phishing toolkit called Gophish. DarkCrystal RAT (aka DCRat) and a previously undocumented remote access trojan called PowerRAT.
“The campaign includes modular infection chains, which are Maldoc or HTML-based infections and require victim intervention to start the infection chain,” Chetan Raguprasad, Cisco Talos researcher. said in Tuesday’s analysis.
Targeting Russian-speaking users is an estimate derived from the language used in phishing emails, attractive content in malicious documents, links masquerading as Yandex Disk (“disk-yandex(.)ru”), and disguised HTML web pages. like VK, the social network that is predominantly used in the country.
Gofish refers to an open-source phishing framework that allows organizations to test their phishing defenses by using easy-to-use templates and launching email-based campaigns that can then be tracked in near real-time.
The unknown threat actor behind this campaign was observed to use a suite of tools to send phishing messages to their targets and ultimately push DCRat or PowerRAT depending on the initial access vector used: a malicious Microsoft Word or HTML document with embedded JavaScript.
When the victim opens maldoc and includes macros, a fake Visual Basic (VB) macro is executed to extract the HTML application (HTA) file (“UserCache.ini.hta”) and the PowerShell loader (“UserCache.ini”).
The macro is responsible for configuring a Windows registry key so that the HTA file is automatically launched whenever the user logs into their account on the device.
The HTA file, in turn, removes the JavaScript file (“UserCacheHelper.lnk.js”) that is responsible for executing the PowerShell loader. JavaScript is executed by a legitimate Windows binary called “cscript.exe”.
“A PowerShell loader script masquerading as an INI file contains a base64-encoded data blob of the PowerRAT payload, which it decodes and executes in the victim machine’s memory,” Raguprasad said.
The malware, in addition to performing system reconnaissance, collects the drive’s serial number and connects to remote servers located in Russia (94.103.85(.)47 or 5.252.176(.)55) to receive further instructions.
“(PowerRAT) has the functionality to execute other scripts or PowerShell commands at the direction of the (command and control) server, including an attack vector to further infect the victim computer.”
In case no response is received from the server, PowerRAT comes with a function that decodes and executes a built-in PowerShell script. None of the analyzed samples have Base64-encoded strings so far, indicating that the malware is in active development.
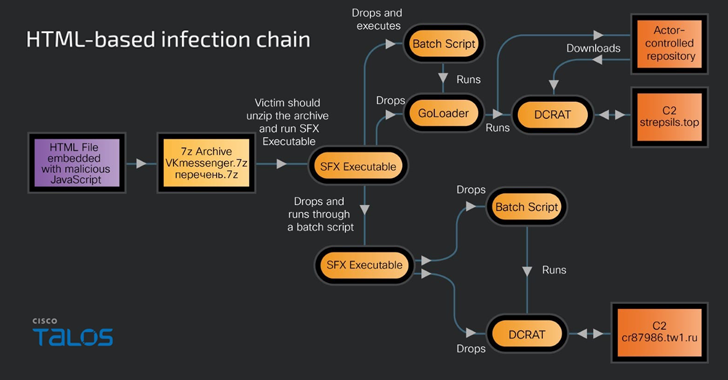
An alternative infection chain that uses HTML files embedded in malicious JavaScript similarly initiates a multi-step process that leads to the deployment of the DCRat malware.
“When a victim clicks on a malicious link in a phishing email, a remote HTML file containing malicious JavaScript opens in the victim’s machine’s browser and executes the JavaScript at the same time,” Talas noted. “JavaScript has a Base64-encoded data blob of a 7-Zip archive of a malicious SFX RAR executable.”
Inside the archive file (“vkmessenger.7z”), which is downloaded using a method called HTML smuggling, is another password-protected SFX RAR containing the RAT payload.
It should be noted that the exact sequence of infection was in detail Netskope Threat Labs in connection with a company that used fake HTML pages posing as TrueConf and VK Messenger to deliver DCRat. In addition, there was the use of a nested self-extracting archive previously observed in the companies that provide SparkRAT.
“The SFX RAR executable is packaged with malicious bootloader or bootloader executables, a batch file and a decoy document in some samples,” Raguprasad said.
“SFX RAR dumps GOLoader and the decoy document’s Excel spreadsheet into the victim machine’s user profiles’ temporary applications folder and launches GOLoader along with opening the decoy document.”
The Golang-based loader is also designed to fetch the DCRat binary data stream from a remote location via a hard-coded URL pointing to the now-remote GitHub repository and save it as “file.exe” in the desktop folder of the victim’s computer.
DCRat is a modular RAT that can steal sensitive data, take screenshots and keystrokes, provide remote access to a compromised system, and facilitate the download and execution of additional files.
“It provides security on the victim computer by creating multiple Windows tasks that will run at different intervals or during the Windows logon process,” Talos said. “The RAT communicates with the C2 server via a URL hard-coded in the RAT configuration file (…) and deletes sensitive data collected from the victim machine.”
This development comes after Cofense warned of phishing campaigns that include malicious content in virtual hard disk (VHD) files as a way to avoid detection by secure email gateways (SEGs) and end up distributing Remcos RAT or XWorm.
“Threat objects send emails with archived .ZIP attachments that contain virtual hard disk files or embedded download links that contain a virtual hard disk file that the victim can plug in and view,” security researcher Kang Ahn. said. “From here, the victim can be misled and launch a malicious payload.”