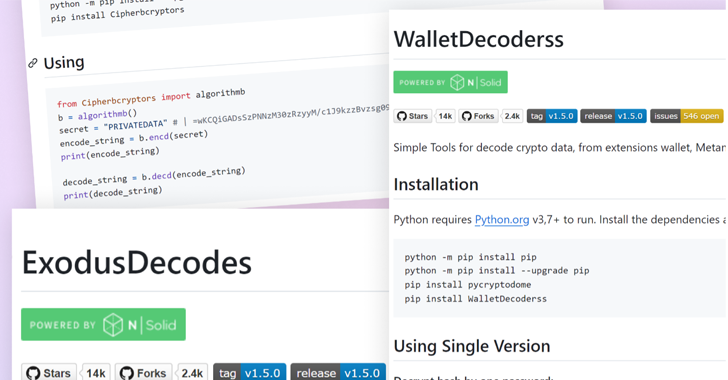
A new set of malicious packages was discovered in the Python Package Index (PyPI) repository, which masqueraded as cryptocurrency wallet recovery and management services with the sole purpose of exfiltrating sensitive data and facilitating the theft of valuable digital assets.
“The attack targeted users of Atomic, Trust Wallet, Metamask, Ronin, TronLink, Exodus and other prominent wallets in the crypto ecosystem,” said Checkmarx researcher Yehuda Gelb. said in Tuesday’s analysis.
“Positioning themselves as utilities for extracting mnemonic phrases and decrypting wallet data, these packages appeared to offer valuable functionality for cryptocurrency users involved in recovery or wallet management.”
However, they contain functionality to steal private keys, mnemonic phrases, and other sensitive wallet data such as transaction history or wallet balance. Each of the packages attracted hundreds of downloads before they were taken down –
Checkmarx said the packages were named as such in a deliberate attempt to attract developers working in the cryptocurrency ecosystem. In a further attempt to lend legitimacy to the libraries, package descriptions on PyPI were accompanied by installation instructions, usage examples, and in one case even “best practices” for virtual environments.
The scam didn’t stop there, as the threat actor behind the campaign also managed to display fake download statistics, giving users the impression that the packages are popular and trustworthy.
Six of the identified PyPI packages included a dependency called cipherbcryptors to execute malicious code, while several others relied on an additional package called ccl_leveldbases in an apparent attempt to obfuscate the functionality.
A distinctive aspect of the packages is that the malicious functionality is only triggered when certain functions are called, marking a denture from a typical template where such behavior is activated automatically on installation. The received data is then transmitted to a remote server.
“The attacker used an extra layer of security by not hard-coding the address of his management server in any of the packets,” Gelb said. “Instead, they used external resources to dynamically retrieve this information.”
This technique, so-called dead drop resolutionallows attackers to update server information without having to update the packages themselves. It also eases the process of migrating to another infrastructure in the event of a server shutdown.
“The attack exploits the trust in open source communities and the apparent utility of wallet management tools, potentially affecting a wide range of cryptocurrency users,” Gelb said.
“The complexity of the attack – from its deceptive packaging to its dynamic malicious capabilities and exploiting malicious dependencies – underscores the importance of comprehensive security measures and constant monitoring.”
This development is just the latest in a series of malicious campaigns targeting the cryptocurrency sector, where threat actors are constantly looking for new ways to siphon funds from victims’ wallets.
In August 2024, details emerged of a sophisticated cryptocurrency scam called CryptoCore, which involves using fake videos or hacked accounts on social media platforms such as Facebook, Twitch, X and YouTube to lure users into parting with their cryptocurrency assets under the guise of a quick and easy profit.
“This fraud group and its distribution companies use deepfake technology, hacked YouTube accounts, and professionally designed websites to trick users into sending their cryptocurrencies to scammers’ wallets,” — Martin Chlumecki, Avast researcher. said.
“The most common method is to convince a potential victim that messages or events posted online are official messages from a trusted social media account or event page, thereby maintaining the credibility associated with the chosen brand, person or event” .
Then last week, Check Point shed light on a rogue Android app that impersonated the legitimate open-source WalletConnect protocol to steal approximately $70,000 in cryptocurrency by initiating fraudulent transactions from infected devices.