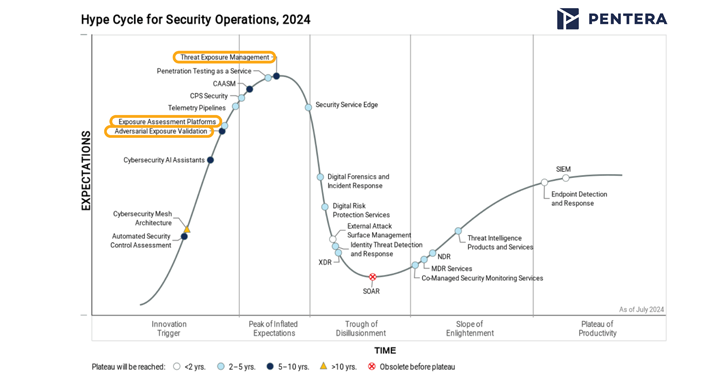
Want to know what’s new and best in SecOps for 2024? The recently published Gartner Hype Cycle for Security Operations report takes important steps to organize and evolve the field of Continuous Threat Exposure Management, also known as CTEM. This year’s report includes three categories in this area: infection management, infection assessment platforms (EAPs) and adversarial infection verification (AEV).
These category definitions are intended to provide some structure to the changing landscape of exposure management technologies. Pentera, listed as a sample provider in the newly defined category, AEV is playing a key role in expanding the adoption of CTEM with an emphasis on safety verification. Below is our take on the CTEM-related product categories and what they mean for security business leaders.
The industry is maturing
Created by Gartner in 2022, CTEM provides a structured approach to continuously assess, prioritize, validate, and remediate the impact of an organization’s attack surface, enabling enterprises to mobilize responses to the most critical risks. The structure it creates helps make the ever-growing attack surface manageable.
A recent reorganization of the categories aims to help businesses identify the security vendors best suited to support Implementation of CTEM.
Threat exposure management is a common set of technologies and processes used to manage threat exposure under the direction of the CTEM program. It includes two new CTEM-related categories described below.
Vulnerability Assessment and Vulnerability Prioritization technology capabilities have been combined into one new category, Exposure Assessment Platforms (EAPs). EAP aims to optimize vulnerability management and improve operational efficiency, no doubt why Gartner gave this category a high preference rating.
Meanwhile, Adversarial Exposure Validation (AEV) combines breach and attack simulation (BAS) with automated pentesting and Red Teaming into one new feature that focuses on providing continuous, automated proof of exposure. AEV is expected to gain major market growth due to its ability to test cyber resilience from a adversarial perspective, challenging an organization’s IT defenses with real-world attack techniques.
What do EAPs offer?
A few things, but for starters they make you less dependent on CVSS scores to prioritize vulnerabilities. While an indicator is useful, that’s all it is, an indicator. A CVSS score does not indicate how exploitable a vulnerability is in the context of your specific environment and threat landscape. The data presented in EAP settings is much more contextualized with threat and asset importance information. It delivers insights in a way that supports action, not oceans of data points.
This additional contextualization also means that vulnerabilities can be labeled in terms of business risk. Need to fix a poorly configured device that no one ever uses and isn’t connected to anything? EAPs help focus efforts on vulnerabilities that aren’t just exploitable, but actually lead to business-critical assets, either for their data or business continuity.
The value of AEV?
While EAPs use scans and data sources to provide exposure context, they are limited to theoretical data analysis without actual evidence of exploitable attack paths. And this is where the AEV comes in, it confirms the exposure from the enemy’s point of view. AEV involves running adversarial attacks to find out what security holes are actually exploitable in your particular environment and how far an attacker would go if they were exploited.
In short, AEV takes threats from the playbook to the playing field.
But there are other benefits; this makes managing the red team much easier. Red teams need a unique set of talents and tools that are difficult to develop and acquire. Having an automated AEV product to handle many red team tasks helps lower that barrier of entry, giving you a more than decent base from which to build.
AEV also helps make a large attack surface more manageable. Relieving the burden on security staff, automated test runs can be run regularly, consistently, and across multiple locations, allowing any willing red team to focus only on priority areas.
Where the brutal goes
It’s not all a bed of roses, there are some thorns that companies need to trim in order to realize the full potential of their threat management initiatives.
When it comes to EAP, it’s important to think beyond compliance and CVSS. A mental shift from viewing assessments as tick-box activities is required. In this limited context, vulnerabilities are listed as isolated threats, and you end up missing the difference between knowing that vulnerabilities exist and prioritizing those vulnerabilities based on their exploitability and potential impact.
For AEV, one challenge is finding the right technology solution that will cover all the bases. Although many vendors offer attack simulation and/or automated penetration testing, they are generally considered separate functions. Security teams that want to validate both the true effectiveness of their security controls and the true exploitability of security vulnerabilities may choose to implement multiple products individually.
The Going Get Proactive
The evolution of the CTEM framework since its introduction two years ago indicates a growing recognition of the critical need for proactive risk mitigation thinking. The new categorization introduced in Hype Cycle reflects the growing maturity of products in this space, supporting the CTEM operation.
When it comes to the AEV category, our recommendation is to use a solution that will seamlessly integrate BAS and penetration testing capabilities, as this is not a common feature for most tools. Look for agentless technologies that closely replicate attacker methods and ease operational requirements. This unique combination ensures that security services can continuously test their security posture with real relevance.
Learn more about how Pentera is used as an important element of any CTEM strategy, enabling enterprises to maintain a robust and dynamic security posture that is constantly tested against the latest threats.
For more information on Continuous Threat Exposure Management (CTEM), join us at the XPOSURE 2024 Summitheld by Pentera, and capture Gartner® 2024 Hype Cycle for Security Operations the report