The Computer Emergency Response Team of Ukraine (CERT-UA) has warned new phishing attacks aimed at infecting devices with malware.
The activity was attributed to the threat cluster it tracks as UAC-0020, which is also known as Paradisi. The exact scale and scope of the attacks are still unknown.
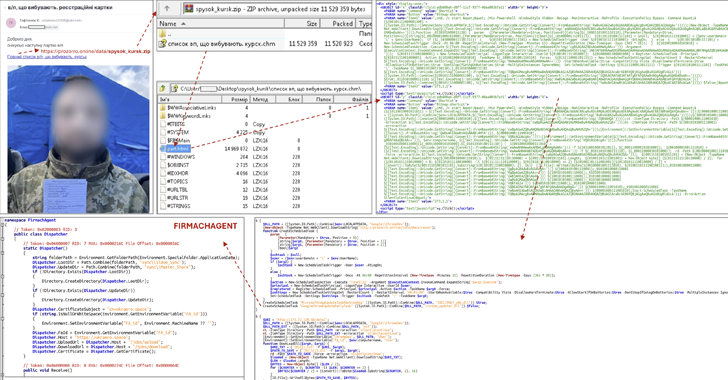
The chain of attacks begins with phishing messages containing photos of alleged POW(s) from Kursk Oblast, urging recipients to click on a link that points to a ZIP archive.
The ZIP file contains a Microsoft Compiled HTML Help (CHM) file that embeds the JavaScript code responsible for running the obfuscated PowerShell script.
“Opening the file installs components of the well-known SPECTR spyware, as well as a new malware called FIRMACHAGENT,” CERT-UA said. “FIRMACHAGENT’s goal is to retrieve data stolen by SPECTR and send it to a remote control server.”
SPECTR is a known malware associated with Vermin back in 2019. It is believed that the group is connected to the security forces of the Luhansk People’s Republic (LPR).
Earlier this June, CERT-UA detailed another campaign called SickSync, organized by members of Vermin, that targeted the nation’s defense forces using SPECTR.
SPECTR is a full-featured tool designed to collect a wide range of information, including files, screenshots, credentials, and data from various instant messaging programs such as Element, Signal, Skype, and Telegram.