Attackers use a cloud-based attack tool called Xeon Sender to conduct large-scale SMS phishing and spam campaigns, abusing legitimate services.
“Attackers can use Xeon to send messages through multiple software-as-a-service (SaaS) providers using valid credentials for the service providers,” SentinelOne security researcher Alex Delamotte. said in a report shared with The Hacker News.
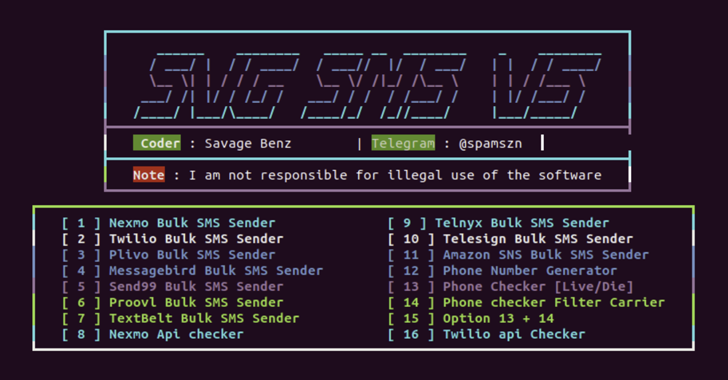
Examples of services used to facilitate bulk SMS messaging include Amazon Simple Notification Service (SNS), Nexmo, Plivo, Proovl, Send99, Telesign, Telnyx, TextBelt, Twilio.
It is important to note here that this activity does not exploit the weaknesses inherent in these providers. Most likely, the tool uses legitimate APIs to carry out mass SMS spam attacks.
It combines tools such as SNS sender which are increasingly becoming a way to bulk ship smiling messages and ultimately capturing sensitive information from targets.
Spread through Telegram and hacker forums, one of the older versions mentions a Telegram channel dedicated to promoting hacked hacking tools. The latest version, available for download as a ZIP file, attributes itself to a Telegram channel under the name Orion Toolxhub (oriontoolxhub), which has 200 members.
Orion Toolxhub was created on February 1, 2023. It has also made other brute force attack software, reverse IP lookup, and more available for free, such as a WordPress site scanner, a PHP web shell, a bitcoin clipper, and a program called YonixSMS that allegedly offers unlimited SMS capabilities.
Xeon Sender is also called XeonV5 and SVG Sender. Early versions of the Python-based program were discovered as early as 2022. Since then, several threat actors have repurposed it for their own purposes.
“Another incarnation of the tool is hosted on a web server with a graphical interface,” Delamotte said. “This hosting method removes a potential barrier to access, allowing less skilled entities that may be uncomfortable working with Python tools and removing their dependencies.”
Xeon Sender, regardless of the variant used, offers its users a command-line interface that can be used to communicate with the server APIs of the chosen service provider and organize mass SMS spam attacks.
It also means that the threat actors already have the necessary API keys needed to access the endpoints. The generated API requests also include the sender ID, message content, and one of the phone numbers selected from a predefined list present in the text file.

Xeon Sender, in addition to SMS sending methods, includes functions to verify Nexmo and Twilio account credentials, generate phone numbers for a given country code and city code, and verify that the phone number is valid.
Despite the lack of subtlety associated with the tool, SentinelOne said the source code is littered with ambiguous variables, such as single letters or a letter plus a number, to make debugging much more difficult.
“Xeon Sender makes heavy use of vendor-specific Python libraries to make API requests, which creates interesting discovery challenges,” Delamotte said. “Each library is unique, as are the vendor’s journals. It can be difficult for teams to detect abuse of this service.”
“To protect against threats like Xeon Sender, organizations should monitor activity related to evaluating or changing permissions to send SMS or abnormal changes to mailing lists, such as large downloads of new recipient phone numbers.”