According to the latest research on employee exit70% of IT professionals say they’ve experienced the negative impact of an incomplete IT shutdown, whether it’s a security incident involving an account that wasn’t shut down, an unexpected bill for resources that are no longer in use, or a missed handover of a critical resource or account. This is despite the fact that each departing employee spends an average of five hours on activities such as locating and disabling SaaS accounts. As the number of SaaS in most organizations continues to expand, it becomes increasingly difficult (and time-consuming) to ensure that all access is disabled or transferred when an employee leaves the organization.
How Nudge Security can help
Nudge Security is a SaaS management platform for modern IT management and security. It discovers every cloud and SaaS account ever created by anyone in your organization, including generative AI applications, giving you a single source of truth for user accounts that are leaving and OAuth grants that need to be revoked , withdraw or transfer.
And the built-in tutorial guides you through a complete checklist for IT offboarding in accordance with Google and Microsoft best practices. The tutorial can help you save up to 90 percent of the time and effort spent on SaaS shutdowns by automating time-consuming, easy-to-miss tasks like revoking OAuth grants and resetting passwords for non-single sign-on (SSO) accounts.
Let’s see how Nudge Security helps you every step of the way so you can ensure complete removal of SaaS accounts.
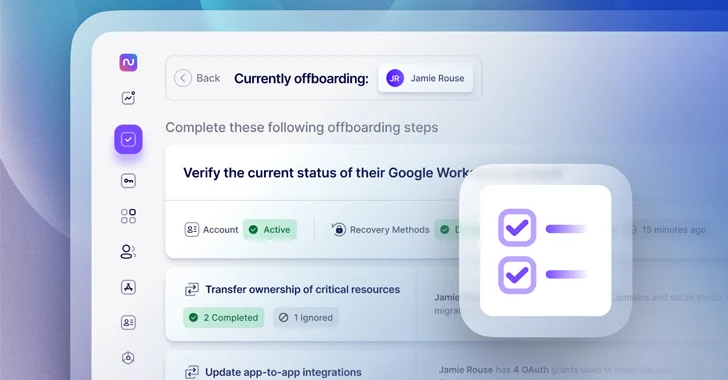
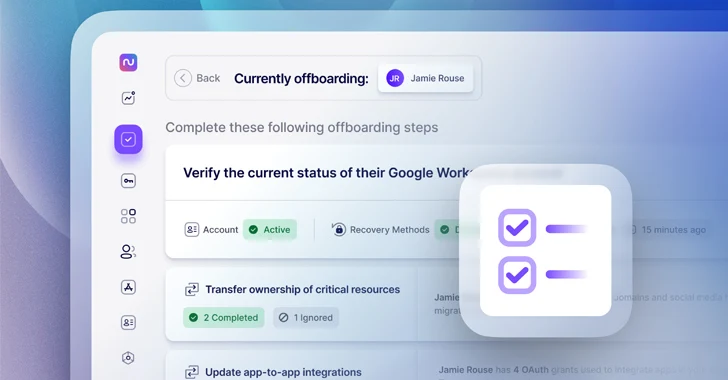
1. Cancel access to Google Workspace or Microsoft 365
Once you’ve selected an employee to leave, the first step is to check the status of their Google or Microsoft account.
Initially, you’ll want to keep the employee’s Google or Microsoft account active while you do other tasks. However, you want to make sure the user can no longer access the account by resetting the password and disabling any recovery methods they may have set up. Nudge Security will help you check the status of each of these steps so you can verify that access has been revoked.
2. Transfer ownership of critical resources.
Before you begin de-initializing departing employee accounts, you’ll want to identify and transfer ownership of critical resources such as AWS root user accounts, corporate domains, social media accounts, and more.
Nudge Security automatically identifies critical resources owned by your departing employee and helps you transfer ownership to other team members. For each resource, Nudge Security provides detailed instructions with helpful links and a summary of other users of the program who can take responsibility for each resource. By browsing the list, you can confirm that you have transferred ownership or record your decision to ignore a particular resource that should not be transferred.
3. Review and update integration between apps.
OAuth grants are often used to enable integration and automation between applications, so if a departing employee’s OAuth permissions are revoked without consideration, it can disrupt day-to-day operations.
Nudge Security shows you all grants and OAuth capabilities on an app-by-app basis for the departing employee, so you can evaluate the potential business impact of each integration and determine whether it should be renewed with a different account. You’ll also see who the other users of this app are, so you can engage them if needed. This step in the exit process will help ensure that automated business processes continue to function properly after an employee leaves the organization.
4. Revoke SSO managed accounts.
This step is easy. With the click of a button (and without leaving the Nudge Security dashboard), you can revoke access to all accounts managed by your single sign-on (SSO) provider, such as Azure AD or Okta. Later, the tutorial will also guide you through cleaning up the contents of these accounts.
5. Revoke access to apps that authenticated via OAuth.
OAuth grants make it easy for employees to create new accounts by simply selecting an authentication option in Google Workspace or Microsoft 365. Nudge Security makes it just as easy for security and IT to identify and revoke OAuth permissions from departing users directly from Nudge Security. . Now that you’ve reviewed and restored any areas related to cross-app integration, you can revoke the rest of the app’s access granted via OAuth.
6. Revoke access to unmanaged accounts.
OAuth grants and SSO-managed accounts only provide partial visibility into your departing employee’s access. Protracted SaaS deployment can leave the door open to illegitimate access to sensitive resources and data after an employee leaves your organization. Fortunately, Nudge Security also inventories unmanaged accounts that your employee may have created with their work email outside of standard IT or procurement processes.
Not only will Nudge Security show you a list of unmanaged programs, but you can trigger an automatic password reset from the platform to prevent further access by the departing employee. Without this automation, it can take hours to do this manually, even if you even know the accounts exist.
7. Clean up revoked accounts.
After a user’s access has been revoked, it is important to clean up their accounts to avoid losing corporate data or continuing to pay for unused licenses.
Nudge Security allows you to send an automated “nudge” to the technical or business owner for each SaaS application with instructions to delete or move sensitive data, reallocate licenses, and reassign resource ownership to another user.
8. Document shutdown activity with built-in reporting.
Nudge Security records all the shutdown steps you take, so you can always go back and check what was done for each employee. Once you’ve finished deleting the departing employee’s SaaS and cloud accounts, you can create a PDF report of what you’ve done and share it with internal users or auditors.
Employee migration is seamless with Nudge Security
Nudge Security effectively and completely off-boards departing users, allowing you to protect corporate resources and avoid business disruptions without wasting valuable time on tedious, repetitive tasks.