A large-scale ransomware campaign compromised various organizations by exploiting publicly available environment variable (.env) files containing credentials related to cloud and social networking applications.
“Several security errors were made during this campaign, including the following: exposing environment variables, using long-lived credentials, and not having a least-privilege architecture,” Palo Alto Networks Division 42. said in a report on Thursday.
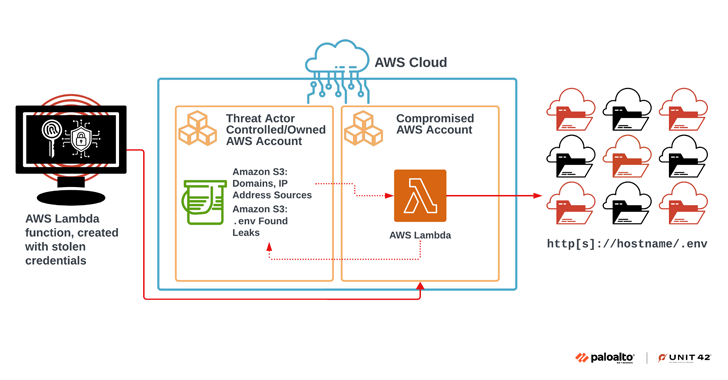
The company is notable for installing its attack infrastructure in infected organizations’ Amazon Web Services (AWS) environments and using them as a launch pad to scan more than 230 million unique targets for sensitive data.
Of the 110,000 domains targeted, the malicious activity is said to have resulted in more than 90,000 unique variables in .env files, of which 7,000 belonged to organizations’ cloud services and 1,500 variables associated with social media accounts.
“The campaign involved attackers successfully ransoming data hosted on cloud storage containers,” said Unit 42. “The event did not involve attackers encrypting data prior to ransom, but rather they stole data and placed a ransom note in a compromised cloud storage container storage”.
The most striking aspect of the attacks is that they do not rely on security vulnerabilities or misconfigurations in cloud provider services, but rather result from the accidental disclosure of .env files in unprotected web applications to gain initial access.
A successful cloud breach paves the way for extensive discovery and reconnaissance steps to expand their base, with threat actors using AWS Identity and Access Management (IAM) access keys to create new roles and elevate their privileges.
The new IAM role with administrative permissions is then used to create new AWS Lambda functions to initiate an automated crawl operation across the internet containing millions of domains and IP addresses.
“The script obtained a list of potential targets from a publicly available third-party S3 package used by the threat,” said Unit 42 researchers Margaret Zimmerman, Sean Johnston, William Gamazo and Nathaniel Quist.
“The list of potential targets that the malicious lambda function was traversing contained an entry for victim domains. For each domain in the list, the code performed a cURL request directed at any environment variable files opened in that domain (for example, https://
When the target domain hosts an open environment file, the plaintext credentials contained in the file are extracted and stored in a newly created folder in another AWS S3 public bucket controlled by the threat actor. The bucket has since been removed by AWS.
The attack campaign was found to specifically highlight instances where .env files contained Mailgun credentials, indicating an adversary’s attempt to use them to send phishing emails from legitimate domains and bypass security measures.

The infection chain ends with the threat actor stealing and deleting sensitive data from the victim’s S3 container and uploading a ransom note urging them to contact and pay a ransom to avoid selling the information on the dark web.
The financial motive behind the attack is also evident in the threat actor’s failed attempts to create new Elastic Cloud Compute (EC2) resources for illegal cryptocurrency mining.
It’s currently unclear who is behind the campaign, partly due to the use of VPNs and the TOR network to hide their true origins, although Unit 42 said it discovered two IP addresses that were geolocated to Ukraine and Morocco as part of a lambda function . and S3 exfiltration activity, respectively.
“The attackers behind this campaign likely used extensive automation techniques to operate successfully and quickly,” the researchers said. “This indicates that these groups of threat actors are skilled and knowledgeable in advanced cloud architecture processes and techniques.”