Duplicated newly discovered attack vector in GitHub Actions artifacts ArtiPACKED can be used to capture storage and gain access to organizations’ cloud environments.
“A combination of misconfigurations and security flaws can lead to token artifacts leaking from both third-party cloud services and GitHub tokens, making them available for use by anyone with read access to the repository,” Yaran Avital, Division 42 Researcher at Palo Alto Networks . said in a report released this week.
“This allows attackers with access to these artifacts to potentially compromise the services these secrets provide access to.”
The cybersecurity firm said it primarily observed the leak of GitHub tokens (such as GITHUB_TOKEN and ACTIONS_RUNTIME_TOKEN), which could not only give attackers unauthorized access to repositories, but also allow them to poison source code and push it into production. through CI/CD workflows.
Artifacts on GitHub to allow users can share data between jobs in a workflow and retain that information for 90 days after it’s completed. This can include builds, log files, kernel dumps, test results, and deployment packages.
The security issue here is that these artifacts are publicly available in the case of open source projects, making them a valuable resource for mining secrets like GitHub access tokens.
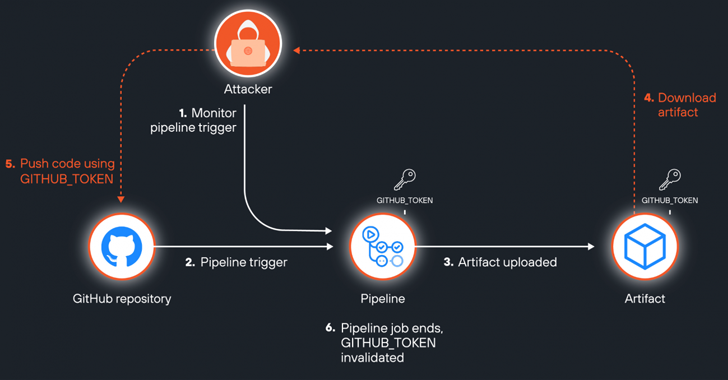
Specifically, the artifacts were found to expose an undocumented environment variable called ACTIONS_RUNTIME_TOKEN, which has a lifetime of about six hours and can be used to replace the artifact with a malicious version before it expires.
This can then open a window of attack for remote code execution if developers directly download and execute a forged artifact or there is a subsequent workflow task configured to execute based on previously downloaded artifacts.
Although the GITHUB_TOKEN expires when the job ends, improvements made to the artifacts feature with version 4 meant that an attacker could use race condition scripts to steal and use the token by loading the artifact during workflow execution.

The stolen token can be used later to push malicious code into the repository by creating a new branch before the pipeline job expires and the token is invalidated. However, this attack targets a worker process that has “content:write” permission.
A number of open source repositories associated with Amazon Web Services (AWS), Google, Microsoft, Red Hat and Ubuntu have been identified as vulnerable to the attack. GitHub, for its part, has classified the issue as informational, requiring users to take responsibility for securing their uploaded artifacts.
“The retirement of GitHub Artifacts V3 should prompt organizations that use the artifacts engine to rethink how they use it,” said Avital. “Overlooked elements, such as build artifacts, are often prime targets for attackers.”