Security vulnerabilities have been discovered in the Ewon Cozy+ industrial remote access solution that can be exploited to gain root privileges on devices and orchestrate subsequent attacks.
Elevated access can then be used to decrypt encrypted firmware files and encrypted data such as passwords in configuration files, and even obtain properly signed X.509 VPN certificates for foreign devices to hijack their VPN sessions.
“This allows attackers to hijack VPN sessions, which creates significant security risks for Cozy+ users and the surrounding industrial infrastructure,” SySS GmbH security researcher Moritz Abrell. said in a new analysis.
There were conclusions presented at the DEF CON 32 conference over the weekend.
The architecture of Ewon Cozy+ involves the use of a VPN connection that goes to a provider-managed platform called Talk2m via OpenVPN. Technicians can remotely connect to the industrial gateway using a VPN relay that happens over OpenVPN.
Germany-based pentest said it had discovered an operating system command injection vulnerability and a filter bypass that allowed a reverse shell to be obtained by downloading a specially crafted OpenVPN configuration.
An attacker could subsequently exploit a persistent cross-site scripting (XSS) vulnerability and the fact that the device stores the credentials of the current web session in Base64 encoding in an insecure credential named cookie to gain administrative access and eventually root it.
“An unauthenticated attacker can gain root access to Cozy+ by combining the vulnerabilities found and, for example, waiting for an admin user to log into the device,” Abrell said.
The attack chain can then be extended to configure security, access firmware encryption keys, and decrypt the firmware update file. Moreover, the hard-encrypted key stored in the password encryption binary can be used to extract secrets.
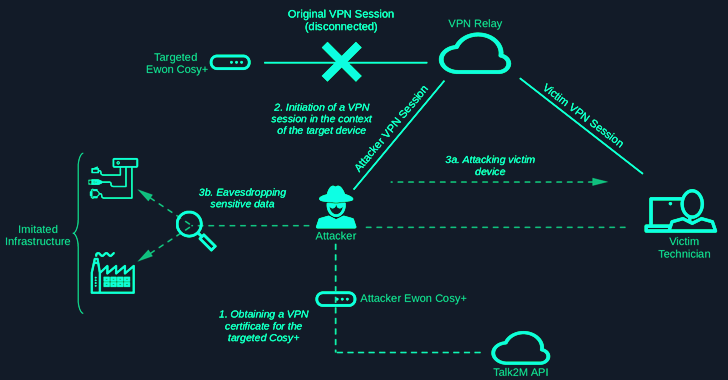
“Communication between Cozy+ and the Talk2m API is done over HTTPS and secured by mutual TLS (mTLS) authentication,” Abrell explained. “When a Cozy+ device is assigned to a Talk2m account, the device generates a Certificate Signing Request (CSR) containing its serial number as the Common Name (CN) and sends it to the Talk2m API.”
This certificate, which the device can access through the Talk2m API, is used for OpenVPN authentication. However, SySS discovered that the sole reliance on the device’s serial number could be used by a threat actor to register their own CSR with the target device’s serial number and successfully initiate a VPN session.

“The original VPN session will be overwritten and therefore the original device is no longer accessible,” Abrell said. “When Talk2m users connect to the device using Ecatcher’s VPN client software, they will be redirected to the attacker.”
“This allows attackers to conduct further attacks against the exploited client, such as accessing network services such as RDP or SMB of the victim client. The fact that the tunnel connection itself is not limited facilitates this attack.”
“As the network communication is redirected to the attacker, the original network and systems can be impersonated to intercept the victim’s user input, such as downloaded PLC programs or similar.”
The development comes as Microsoft uncovered several flaws in OpenVPN that can be combined to achieve remote code execution (RCE) and local privilege elevation (LPE).