Cybersecurity researchers have discovered multiple critical flaws in Amazon Web Services (AWS) offerings that, if successfully exploited, could lead to serious consequences.
“The impact of these vulnerabilities ranges from remote code execution (RCE), full-service user hijacking (which can provide powerful administrative access), manipulation of artificial intelligence modules, exposure of sensitive data, data theft, and denial of service,” it writes Aqua is a cloud security company. according to a detailed report shared by The Hacker News.
After making a responsible disclosure in February 2024, Amazon addressed the deficiencies over several months from March to June. There were conclusions presented at Black Hat USA 2024.
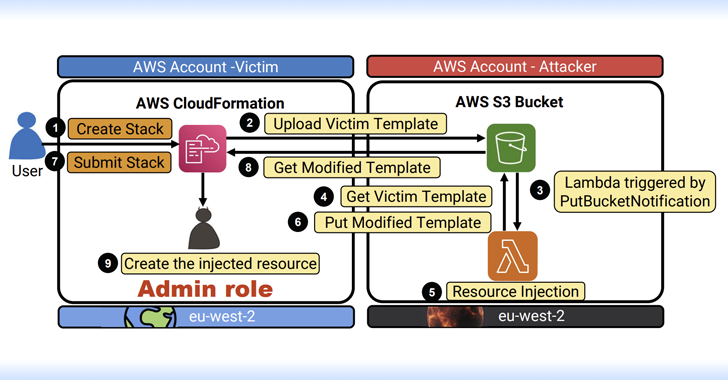
Central to the problem, dubbed Bucket Monopoly, is an attack vector called Shadow Resource, which in this case refers to the automatic creation of an AWS S3 bucket when using services such as CloudFormation, Glue, EMR, SageMaker, ServiceCatalog, and CodeStar.
The S3 bucket name generated in this way is both unique and conforms to the predefined naming convention (“cf-templates-{Hash}-{Region}”). An attacker could take advantage of this behavior to configure a bucket in unused regions of AWS and wait for a legitimate AWS customer to use one of the susceptible services to covertly access the contents of the S3 bucket.
Based on the permissions granted to an adversary-controlled S3 block, this approach can be used to escalate to cause a DoS condition, or execute code, manipulate or steal data, and even gain full control of the victim’s account without the user’s knowledge.
To maximize their chances of success using Bucket Monopoly, attackers can create unclaimed buckets in all available regions in advance and store malicious code in them. When a target organization first enables one of the vulnerable services in a new region, malicious code will be unknowingly executed, which could lead to the creation of an administrative user that could hand control over to attackers.
 |
| CloudFormation Vulnerability Overview |
However, it is important to note that for a successful attack, an attacker would have to wait until the victim first deploys a new CloudFormation stack in a new region. Modifying the CloudFormation template file in the S3 bucket to create a fake admin user also depends on whether the victim account has permission to manage IAM roles.
 |
| Glue Vulnerability Overview |
 |
| CodeStar Vulnerability Review |
Aqua said it discovered five other AWS services that rely on a similar naming methodology for S3 partitions – {Service Prefix}-{AWS Account ID}-{Region}, exposing them to Shadow Resource attacks and ultimately allowing a threat actor to escalate privileges and perform malicious activities, including DoS, information disclosure, data manipulation, and arbitrary code execution –
- AWS Glue: aws-glue-assets-{Account-ID}-{Region}
- AWS Elastic MapReduce (EMR): aws-emr-studio -{Account-ID}-{Region}
- AWS SageMaker: sagemaker-{Region}-{Account-ID}
- AWS CodeStar: aws-codestar-{Region}-{Account-ID}
- AWS Services Directory: cf-templates-{Hash}-{Region}

The company also noted that AWS account IDs should be considered secret, unlike Amazon’s states in their documentation, as they can be used to organize similar attacks.
“This attack vector affects not only AWS services, but also many open source projects used by organizations to deploy resources in their AWS environment,” Aqua said. “Many open source projects automatically create S3 buckets as part of their functionality or instruct their users to deploy S3 buckets.”
“Instead of using predictable or static identifiers in the bucket name, it is preferable to create a unique hash or random identifier for each region and account by including this value in the S3 bucket name. This approach helps protect against attackers who prematurely claim your bucket. .”