Cybersecurity researchers have discovered a new phishing campaign that uses Google Drawings and shortened links created via WhatsApp to avoid detection and trick users into clicking fake links designed to steal sensitive information.
“The attackers chose a group of the most prominent websites in computing to create the threat, including Google and WhatsApp to host the attack elements, and an Amazon lookalike to collect the victim’s information,” Menlo Security researcher Ashwin Vamshi said. “This attack is a great example of life at the expense of trusted sites (a lot) threat”.
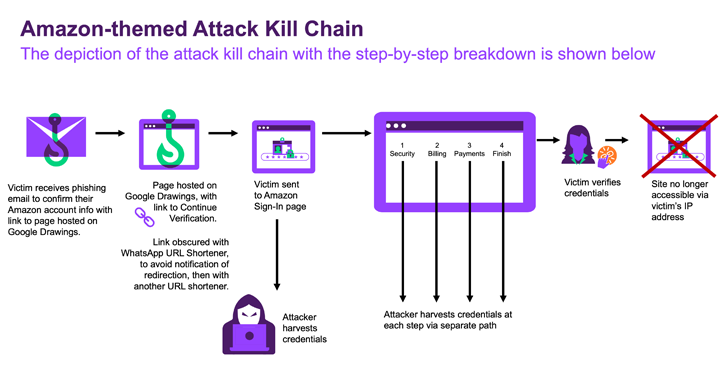
The starting point of the attack is a phishing email that directs recipients to a graphic that looks like an Amazon account verification link. This graphic, for its part, is hosted on Google Drawings, in an apparent attempt to avoid detection.
Abusing legitimate services has the obvious benefit to attackers in that they are not only a low-cost solution, but more importantly, they offer a stealthy way to communicate within networks as they are unlikely to be blocked by security products or firewalls.
“Another thing that makes Google Drawings attractive at the beginning of an attack is that it allows users (in this case, the attacker) to include links in their graphics,” Vamshi said. “Such links can easily go unnoticed by users, especially if they feel a sense of urgency around a potential threat to their Amazon account.”
Users who end up clicking on the verification link are taken to a similar Amazon login page where the URL is sequentially generated using two different URL shorteners – WhatsApp (“l.wl(.)co”) followed by comes qrco(.)de – – as an additional layer of obfuscation and spoofing the security of URL scanners.
The fake page is designed to collect credentials, personal information and credit card details, after which victims are redirected to the original fake Amazon login page. As an additional step, the web page becomes unreachable from the same IP address after the credentials are verified.
The disclosure comes after researchers discovered a loophole in Microsoft 365’s anti-phishing mechanisms that could be abused, increasing the risk of users opening phishing emails.

The method involves using CSS tricks to hide the “First Contact Safety Tip” that warns users when they receive emails from an unknown address. Microsoft, which acknowledged the problem, has yet to release a fix.
“First-contact security advice is added to the body of an HTML email, which means you can change how it’s displayed using CSS style tags,” – Austrian cybersecurity service Certitude. said. “We can go even further and fake the icons that Microsoft Outlook adds to encrypted and/or signed emails.”