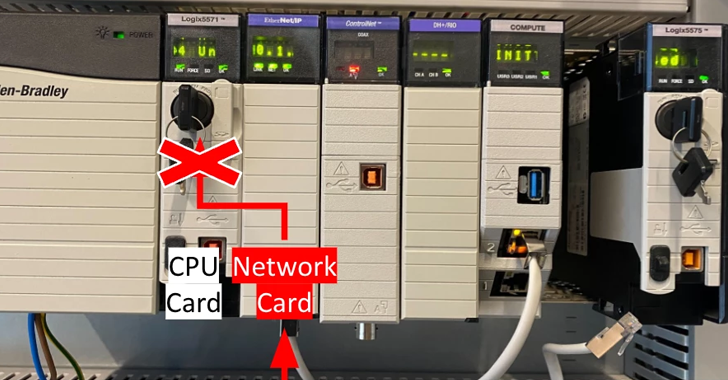
A high security bypass vulnerability has been discovered in Rockwell Automation ControlLogix 1756 devices that could be used to execute a common industrial protocol (CIP) programming and configuration commands.
A vulnerability that is assigned a CVE identifier CVE-2024-6242has a CVSS v3.1 score of 8.4.
“A vulnerability exists in the affected products that could allow a threat actor to bypass the Trusted Slot feature in a ControlLogix controller,” the US Cybersecurity and Infrastructure Security Agency (CISA) said. said in the consulting room.
“When using any compromised module in a 1756 chassis, a threat actor could potentially execute CIP commands that modify user designs and/or device configuration on a Logix controller in the chassis.”
Operational technology security company Claroty, which discovered and reported the vulnerability, said it developed a technique that allowed it to bypass the trusted slot feature and send malicious commands to a programmable logic controller (PLC) processor.

The trusted slot feature “enforces security policies and allows the controller to deny communication over untrusted paths on local chassis“, – security researcher Sharon Bryzinov said.
“The vulnerability we discovered, before it was patched, allowed an attacker to travel between local backplane slots in a 1756 chassis using CIP routing, crossing a security boundary designed to protect the processor from untrusted cards.”
While a successful exploit requires network access to the device, an attacker can use the flaw to send elevated commands, including loading arbitrary logic to the PLC’s processor, even if the attacker is behind an untrusted network card.
After responsible disclosure, the flaw was addressed in the following versions –
- ControlLogix 5580 (1756-L8z) – Upgrade to V32.016, V33.015, V34.014, V35.011 and later.
- GuardLogix 5580 (1756-L8zS) – Upgrade to V32.016, V33.015, V34.014, V35.011 and later.
- 1756-EN4TR – Upgrade to V5.001 and later.
- 1756-EN2T Series D, 1756-EN2F Series C, 1756-EN2TR Series C, 1756-EN3TR Series B, and 1756-EN2TP Series A – Upgrade to V12.001 or later
“This vulnerability could have exposed critical control systems to unauthorized access via the CIP protocol originating from untrusted chassis slots,” Bryzinov said.