In another sign that threat actors are always looking for new ways to trick users into downloading malware, it emerged that a question-and-answer (Q&A) platform known as Stack Exchange was used to direct unsuspecting developers to fake Python packages capable of drain their cryptocurrency wallets.
“Once installed, this code will execute automatically, triggering a chain of events designed to hack and control the victim’s systems, steal their data and drain their crypto wallets,” Checkmarx researchers Yehuda Gelb and Tzahi Zornstein said in the report shared with The Hacker News.
The campaign, which began on June 25, 2024, specifically singled out cryptocurrency users associated with Raydium and Solana. The list of unauthorized packages detected during this activity is given below –
The packages have been downloaded a total of 2082 times. They are no longer available for download from the Python Package Index (PyPI) repository.

The malware hidden in the package served as a full-fledged information stealer, scattering a wide web of data, including web browser passwords, cookies and credit card details, cryptocurrency wallets and information related to messaging apps such as Telegram, Signal and Session .
It also has the ability to take system screenshots and search for files containing GitHub recovery codes and BitLocker keys. The collected information was then compressed and sent to two different Telegram bots maintained by the criminals.
Separately, the backdoor component present in the malware provided the attacker with permanent remote access to the victim’s machines, allowing for possible future exploits and long-term compromise.
The attack chain spans several steps, with the “raydium” package listing “spl-types” as a dependency in an attempt to hide the malicious behavior and give users the impression that it was legitimate.
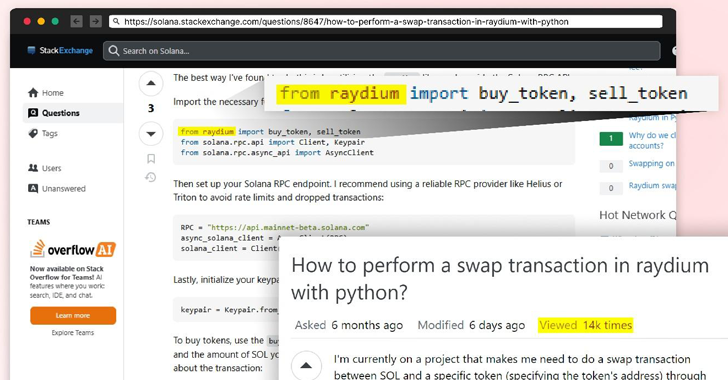
A notable aspect of the campaign is to use Stack Exchange as a vector for adoption by posting supposedly helpful answers with links to the package in question on developer questions related to performing swap transactions in Raydium using Python.
“By choosing a high-visibility thread — racking up thousands of views — the attacker maximized his potential reach,” the researchers said, adding that this was done to “give credibility to this package and ensure its widespread distribution.”
Although the answer no longer exists on Stack Exchange, The Hacker News found references to “raydium” elsewhere an unanswered question posted on Q&A on July 9, 2024: “I’ve been struggling at night to replace a solana mesh running on python 3.10.2, solana, solder and raydium installed, but I can’t get it to work” – the user said.
Links to “raydium-sdk” are also there surfaced in a post titled “How to Buy and Sell Raydium Tokens Using Python: A Solana Step-by-Step Guide” shared by SolanaScribe on the social media platform Medium on Jun 29, 2024.
It is currently unclear when the packages were removed from PyPI, as two other users responded to a Medium post asking the author for help installing “raydium-sdk” as recently as six days ago. Checkmarks told The Hacker News that the message was not the work of the threat author.
This is not the first time criminals have resorted to this method of spreading malware. Earlier in May, Sonatype revealed how a package called pytoileur was promoted through another Q&A service called Stack Overflow to facilitate cryptocurrency theft.
If anything, this event is proof that attackers are exploiting the trust in these community-driven platforms to promote malware, leading to large-scale supply chain attacks.
“One compromised developer can inadvertently introduce vulnerabilities into an entire company’s software ecosystem, potentially affecting the entire corporate network,” the researchers said. “This attack serves as a wake-up call for both individuals and organizations to rethink their security strategies.”
The development comes after Fortinet FortiGuard Labs detailed a malicious PyPI package called zlibxjson that contains features to steal sensitive information such as Discord tokens, cookies stored in Google Chrome, Mozilla Firefox, Brave and Opera, and saved passwords from browsers. The library attracted a total 602 downloads before it was pulled from PyPI.
“These actions can lead to unauthorized access to user accounts and theft of personal data, clearly classifying the software as malicious,” security researcher Jenna Wang. said.