A now-patched security flaw in Microsoft Defender SmartScreen has been exploited by a new information-stealing campaign, such as ACR Stealer, Lammaand Medusa.
Fortinet’s FortiGuard Labs says it has discovered a phishing campaign targeting Spain, Thailand and the US using file-mines that use CVE-2024-21412 (CVSS Score: 8.1).
High Severity Vulnerability allows attacker to bypass SmartScreen protection and delete malicious payloads. Microsoft addressed this issue in the monthly security updates released in February 2024.
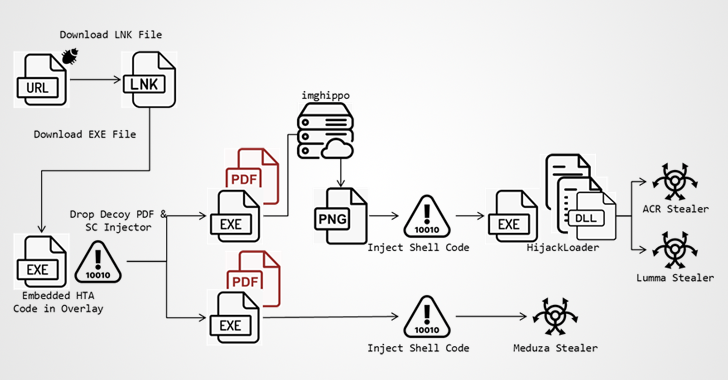
“At first, attackers encourage victims to follow a crafted link to a URL designed to download an LNK file,” security researcher Kara Lin said. “The LNK file then loads an executable file containing the script (HTML Application).”

The HTA file serves as a conduit for decoding and decrypting the PowerShell code responsible for obtaining the fraudulent PDF file and the shellcode injector, which in turn leads to the deployment of the Meduza Stealer or Hijack bootloaderwhich then launches ACR Stealer or Lumma.
ACR Stealer, evaluated as an improved version of GrMsk Stealer, was announced in late March 2024 by a threat actor named SheldIO on the Russian-language underground RAMP forum.
“This ACR heist hides its (command and control) dead spot review (DDR) technique on the Steam community website,” Lin said, citing its ability to sift through web browsers, crypto wallets, messaging programs, FTP clients, email clients, VPN services and password managers.
It should be noted that recent Lumma Stealer attacks have also been seen using the same technique, making it easier for adversaries to change C2 domains at any time and making the infrastructure more resilient. respectively at the AhnLab Security Intelligence Center (ASEC).
Disclosure is happening, as is CrowdStrike revealed that threat actors use shutdown last week distribute a previously undocumented information stealer called Daolpu, making it the latest example precipitation continues stems from a botched update that crippled millions of Windows devices.
The attack involves using a Microsoft Word document with firmware that is disguised as a list of Microsoft recovery guides legal instructions issued by the Windows manufacturer to solve the problem by using it as a decoy to activate the infection process.
The DOCM filewhen opened, runs a macro to retrieve a second-stage DLL from the remote control, which is decoded to launch Daolpu, a stealth malware designed to harvest credentials and cookies from Google Chrome, Microsoft Edge, Mozilla Firefox, and other Chromium-based browsers.
It’s also worth an appearance new families of stealing malware such as Braodo and DeerStealer, even as cybercriminals use malvertising techniques promoting legitimate software such as Microsoft Teams to deploy Atomic Stealer.
“As cybercriminals ramp up their distribution campaigns, downloading apps through search engines is becoming increasingly dangerous,” said Jerome Segura, researcher at Malwarebytes. said. “Users must navigate between malicious ads (sponsored results) and SEO poisoning (compromised websites).”