A Chinese-related threat called APT17 was spotted attacking Italian companies and government organizations using a variant of a well-known malware called the 9002 RAT.
The two targeted attacks took place on June 24 and July 2, 2024, Italian cybersecurity firm TG Soft said in an analysis published last week.
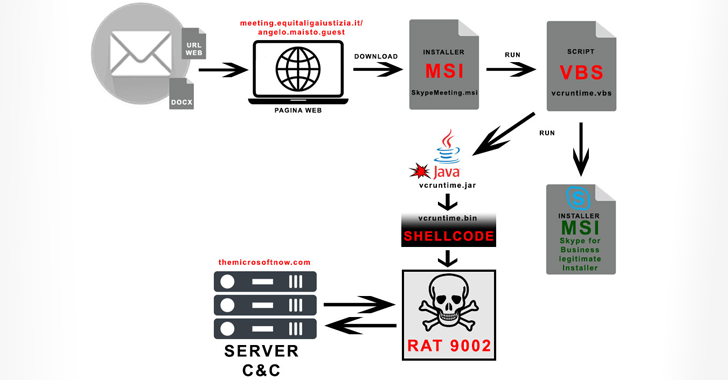
“The first campaign used an Office document on June 24, 2024, and the second campaign contained a link,” the company said in a statement. noted. “Both companies invited the victim to install the Skype for Business package on an Italian government domain link in order to transmit variant 9002 of the RAT.”

APT17 was first documented by Google-owned Mandiant (then FireEye) in 2013 as part of a cyber espionage operation called Deputy Dog and Ephemeral hydra which used zero-day flaws in Microsoft’s Internet Explorer to compromise interesting targets.
He also goes by the aliases Aurora Panda, Bronze Keystone, Dogfish, Elderwood, Helium, Hidden Lynx, and TEMP.Avengers, not to mention sharing some of the same toolkit with another threat actor named Web worm.
9002 RATaka Hydraq and McRAT, gained fame as cyber weapons with choice in Operation Aurora. highlighted Google and other large companies in 2009. It was subsequently used in another campaign in 2013 under the title Solar shop in which attackers injected malicious redirects to several websites.
Recent attack chains involve the use of phishing lures to get recipients to click on a link that prompts them to download the Skype for Business MSI installer (“SkypeMeeting.msi”).
Running the MSI package starts the execution of the Java Archive (JAR) file via Visual Basic Script (VBS) and also installs the legitimate chat software on the Windows system. The Java application, in turn, decodes and executes the shellcode responsible for running the 9002 RAT.
A modular trojanThe 9002 RAT comes with features for monitoring network traffic, taking screenshots, listing files, managing processes, and executing additional commands received from a remote server to facilitate network discovery, among other things.
“The malware appears to be constantly updated with diskless variants,” TG Soft said. “It consists of various modules that are activated as needed by a cyber actor to reduce the possibility of interception.”