Cybersecurity researchers have shed light on a new version of ransomware called HardBit that comes bundled with new obfuscation techniques to thwart analysis attempts.
“Unlike previous versions, the HardBit Ransomware team has improved version 4.0 with passphrase protection,” Cybereason researchers Kotaro Ogino and Koshi Oyama said in the analysis.
“The passphrase must be entered at runtime for the ransomware to launch properly. Additional obfuscation prevents security researchers from analyzing the malware.”
HardBit, which appeared for the first time in October 2022 is a financially motivated threat that, like other ransomware groups, operates to generate illicit revenue through a two-pronged extortion tactic.
What sets the threat group apart is that it does not operate the data breach site, but instead makes victims pay by threatening to carry out additional attacks in the future. His primary mode of communication is through the instant messaging service Tox.
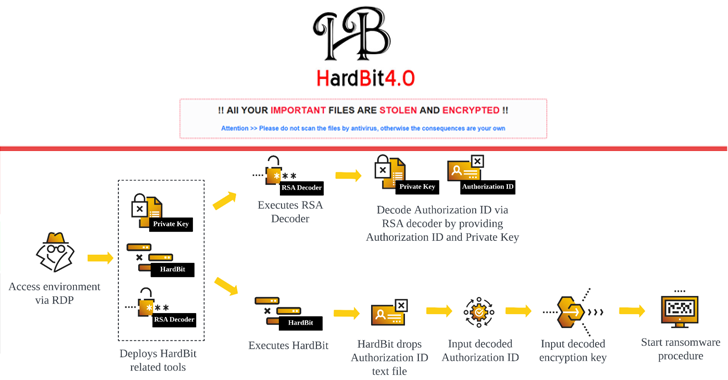
The exact initial access vector used to compromise the target environments is currently unclear, although it is suspected to include RDP and SMB services by hijacking.
The next steps include stealing credentials with tools like Mimikatz and NLBrute, and network discovery with utilities like Advanced Port Scanner, allowing attackers to navigate the network laterally using RDP.
“Once the victim host is compromised, the HardBit ransomware payload executes and performs a series of steps that degrade the security of the host before encrypting the victim’s data,” Voronis. noted in its technical description of HardBit 2.0 last year.
Encrypting the victim hosts is done by deploying HardBit, which comes with a known file infector virus called Something. It should be noted that Neshta has also been used by threat actors in the past distribute Big Head ransomware.
HardBit is also designed to disable Microsoft Defender Antivirus and stop processes and services to avoid potential detection of its activities and prevent system recovery. It then encrypts the files of interest, updates their icons, changes the desktop wallpaper, and changes the system volume label to “Locked by HardBit.”
In addition to being offered to the operator in command-line or GUI versions, the ransomware requires an authorization ID to run successfully. The GUI additionally supports a cleanup mode for permanent file deletion and disk cleanup.
“After threat actors successfully enter the decoded authorization ID, HardBit requests an encryption key to encrypt files on target machines and continues the ransomware process,” Cybereason noted.
“The HardBit ransomware group needs to enable the wipe mode feature, and this feature is most likely an optional feature that operators will have to buy. If the operator wants cleanup mode, the operator will need to deploy hard.txt, the optional HardBit configuration file is binary and contains the authorization ID to enable cleanup mode.”
The development comes as cybersecurity firm Trellix in detail a CACTUS ransomware attack that was seen exploiting security flaws in Ivanti Sentry (CVE-2023-38035) to install file-encrypting malware using legitimate remote desktop tools like AnyDesk and Splashtop.

Ransomware activity continues to “maintain an upward trend” in 2024, with ransomware actors reporting 962 attacks in the first quarter of 2024, compared to 886 attacks reported last year. LockBit, Akiraand black suit Symantec said they became the most common ransomware families during this time period.
According to the 2024 Palo Alto Networks Unit 42 Incident Response Report, average time the need to go from compromise to data breach has dropped dramatically from nine days in 2021 to two days last year. In almost half (45%) of cases this year, it was just under 24 hours.
“Available evidence suggests that exploitation of known vulnerabilities in public applications continues to be the primary vector for ransomware attacks,” the Broadcom-owned company said. said. “Bring your own vulnerable driver (BEUD) continues to be a favorite tactic among ransomware groups, especially as a means of disabling security solutions.”