Unknown threat actors have been observed using a patched security flaw in Microsoft MSHTML to create a tracking tool called BrandSpy within the campaign, primarily targeting users in Canada, India, Poland, and the United States
“MerkSpy is designed to covertly monitor user activity, collect sensitive information, and preserve compromised systems,” Fortinet FortiGuard Labs researcher Kara Lin said in a report published last week.
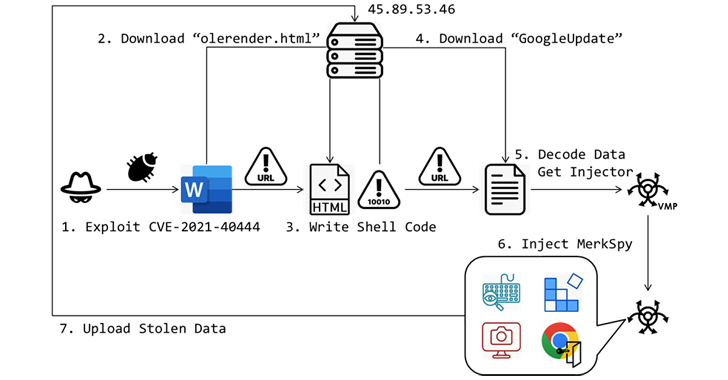
The starting point of the attack chain is a Microsoft Word document that allegedly contains a job description for a software engineer.
But opening the file causes an exploit CVE-2021-40444, a serious flaw in MSHTML that could lead to remote code execution without the need for user interaction. This was resolved by Microsoft as part of the Patch Tuesday updates released in September 2021.
In this case, it opens a path to download an HTML file (“olerender.html”) from the remote server, which in turn initiates the execution of the embedded shellcode after checking the operating system version.
“Olerender.html” takes advantage of “”VirtualProtect”” to change memory access rights, allowing decoded shellcode to be safely written to memory,” Lin explained.
“CreateThread then executes the injected shellcode, setting the stage for the next payload to be downloaded and executed from the attacker’s server.” This process ensures that malicious code runs smoothly, making further exploitation easier.”
The shellcode serves as the downloader for a file that is deceptively named “GoogleUpdate,” but actually contains an injector payload responsible for evading detection by security programs and loading MerkSpy into memory.
Spyware installs persistence on the host through changes to the Windows registry so that it starts automatically when the system starts. It also comes with capabilities to covertly collect sensitive information, monitor user activities, and output data to external servers under the control of threat actors.

This includes screenshots, keystrokes, login credentials stored in Google Chrome, and data from the MetaMask browser extension. All this information is sent to the URL “45.89.53(.)46/google/update(.)php.”
The development comes as Symantec launched a stunningly detailed campaign targeting US users with snippets of SMS messages purporting to be from Apple and intended to trick them into fake credential collection pages (“signin.authen- connexion(.)info/icloud” ) to continue using the services.
“The malicious website is accessible from both desktop and mobile browsers,” the Broadcom-owned company said said. “To add a layer of perceived legitimacy, they implemented a CAPTCHA that users must complete. Users are then directed to a web page that mimics the outdated iCloud login template.”